Emsisoft Decrypter for CryptoPokemon 1.0.0.0
|
Author:
Emsisoft
Date: 04/11/2019 Size: 1.56 MB License: Freeware Requires: Win 10 / 8 / 7 / Vista / XP Downloads: 2541 times Restore Missing Windows Files |
Download@Authors Site Download@MajorGeeks Download@MajorGeeks
|
MajorGeeks: Setting the standard for editor-tested, trusted, and secure downloads since 2001. |
Get free antivirus with AI-powered online scam detection Download Free!
Use Emsisoft Decrypter for CryptoPokemon to decrypt files held by the CryptoPokemon strain of ransomware.
The CryptoPokemon malware uses SHA256 and AES-128 to capture your files, and then adds the extension ".CRYPTOPOKEMON". You are presented with a ransom note and website claiming to be "PokemonGO."
Below is an example of the ransom note !INFO.CRYPTOPOKEMON.log:
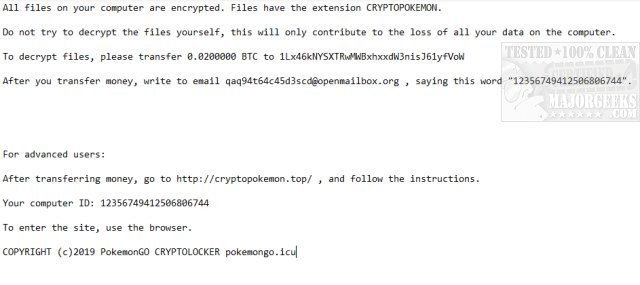
You will need to remove the malware from your system first, otherwise, it will repeatedly lock your system or encrypt files. By default, Emsisoft Decrypter for CryptoPokemon will pre-populate the locations to decrypt with the currently connected drives and network drives. Additional locations can be added via the Add button.
Decrypters typically offer various options depending on the particular malware family. The available options are located in the Options tab and can be enabled or disabled there. After you have added all the locations you want to decrypt to the list, click the “Decrypt” button to start the decryption process. The screen will switch to a status view, informing you about the current process and decryption status of your files.
Emsisoft Decrypter for CryptoPokemon will notify you that the decryption process is complete. If you require a report for your records, you can save it by clicking the Save log button. You also have the option to copy it straight to your clipboard for use in emails, forum posts, etc., if needed.
The CryptoPokemon malware uses SHA256 and AES-128 to capture your files, and then adds the extension ".CRYPTOPOKEMON". You are presented with a ransom note and website claiming to be "PokemonGO."
Below is an example of the ransom note !INFO.CRYPTOPOKEMON.log:

You will need to remove the malware from your system first, otherwise, it will repeatedly lock your system or encrypt files. By default, Emsisoft Decrypter for CryptoPokemon will pre-populate the locations to decrypt with the currently connected drives and network drives. Additional locations can be added via the Add button.
Decrypters typically offer various options depending on the particular malware family. The available options are located in the Options tab and can be enabled or disabled there. After you have added all the locations you want to decrypt to the list, click the “Decrypt” button to start the decryption process. The screen will switch to a status view, informing you about the current process and decryption status of your files.
Emsisoft Decrypter for CryptoPokemon will notify you that the decryption process is complete. If you require a report for your records, you can save it by clicking the Save log button. You also have the option to copy it straight to your clipboard for use in emails, forum posts, etc., if needed.
 Screenshot for Emsisoft Decrypter for CryptoPokemon
Screenshot for Emsisoft Decrypter for CryptoPokemon






 Tactical Briefings
Tactical Briefings