Beware of Malaysia Airlines flight MH17 cyberscams
Posted by: Jon Ben-Mayor on 07/19/2014 08:43 AM
[
 Comments
]
Comments
]
There have been a few reports so far of scams relating to MH17 - but be certain that more will come slinking out of the depths with bold headlines asking you to click and look at crash site videos/pictures or the like.
During Trend Micro's investigation, just a few hours after Malaysian Airline tweeted at 23:36, July 17 “Malaysia Airlines has lost contact of MH17 from Amsterdam. The last known position was over Ukrainian airspace. More details to follow,” we came across some suspicious tweets written in Indonesian:
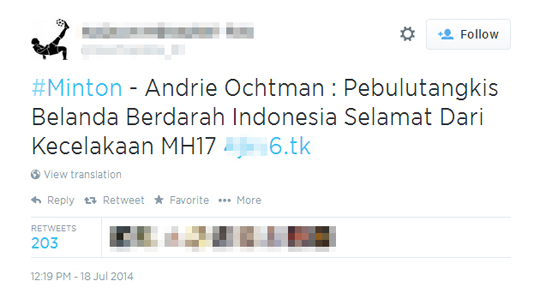
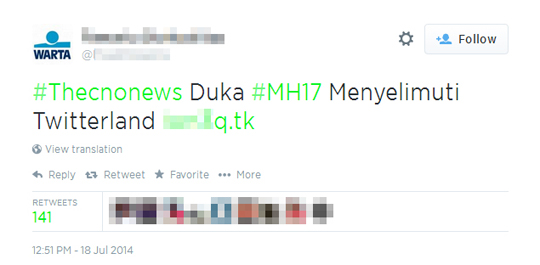
It seems that the URLs are used in a kind of spam where the most talked about topic/hashtag in Twitter is gathered so that it can be easily searched by users. Once clicked by users, their URL count increases. The.TK URLs resolve to the following IPs:
72[dot]8[dot]190[dot]126
72[dot]8[dot]190[dot]39
Based on their analysis, these two IPs are verified to be webhosting/shared IP located in the US.
These IPs are mapped to multiple domains. Some of these domains are malicious while there are other legitimate normal domains hosting blogs. We surmise that this spam is for gaining hits/page views on their sites or ads.
Trend Micro goes on to say that the malicious domains associated with these IPs are connected to a ZeuS variant along with other malware, thus compromising their security.
Be vigilant.
During Trend Micro's investigation, just a few hours after Malaysian Airline tweeted at 23:36, July 17 “Malaysia Airlines has lost contact of MH17 from Amsterdam. The last known position was over Ukrainian airspace. More details to follow,” we came across some suspicious tweets written in Indonesian:


It seems that the URLs are used in a kind of spam where the most talked about topic/hashtag in Twitter is gathered so that it can be easily searched by users. Once clicked by users, their URL count increases. The.TK URLs resolve to the following IPs:
72[dot]8[dot]190[dot]126
72[dot]8[dot]190[dot]39
Based on their analysis, these two IPs are verified to be webhosting/shared IP located in the US.
These IPs are mapped to multiple domains. Some of these domains are malicious while there are other legitimate normal domains hosting blogs. We surmise that this spam is for gaining hits/page views on their sites or ads.
Trend Micro goes on to say that the malicious domains associated with these IPs are connected to a ZeuS variant along with other malware, thus compromising their security.
Be vigilant.
Comments






