Beware of Man-in-the-middle attacks
Posted by: Timothy Weaver on 04/02/2015 09:02 AM
[
 Comments
]
Comments
]
What is a man-in-the-middle attack?
An attack in which an attacker can read, insert and modify messages between two users or systems. Data is sent from point A (computer) to point B (server/website), and an attacker can get in-between these transmissions.
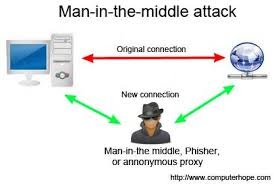 The object of the attack is to get the victim to disclose personal data, such as log in passwords and financial info.
The object of the attack is to get the victim to disclose personal data, such as log in passwords and financial info.
With a traditional MITM attack, the attacker needs to have access to an unsecured, or poorly secured Wi-Fi router. This is most likely to occur at a public Wi-Fi center.
How can you avoid these types of attack? Follow some of the following suggestions:
• Make sure “HTTPS” is always in the URL bar of the websites you visit.
• Be wary of potential phishing emails from attackers asking you to update your password or any other log in credentials. Instead of clicking in the link provided in the email, manually type the website in questions address into the URL bar of your browser and proceed from there.
• Never connect to public Wi-Fi routers directly if possible. You can use a Virtual Private Network (VPN), or you can use a browser plug-in such as HTTPS Everywhere or ForceTLS.
• Since MITB attacks primarily use malware for execution, you should have a comprehensive Internet security solution such as Norton Security installed on your computer, and be sure to keep the program up to date.
• Be sure that your home network is secured. Change all of the default usernames and passwords on your home router and any other equipment.
Source: Norton
An attack in which an attacker can read, insert and modify messages between two users or systems. Data is sent from point A (computer) to point B (server/website), and an attacker can get in-between these transmissions.
 The object of the attack is to get the victim to disclose personal data, such as log in passwords and financial info.
The object of the attack is to get the victim to disclose personal data, such as log in passwords and financial info.With a traditional MITM attack, the attacker needs to have access to an unsecured, or poorly secured Wi-Fi router. This is most likely to occur at a public Wi-Fi center.
How can you avoid these types of attack? Follow some of the following suggestions:
• Make sure “HTTPS” is always in the URL bar of the websites you visit.
• Be wary of potential phishing emails from attackers asking you to update your password or any other log in credentials. Instead of clicking in the link provided in the email, manually type the website in questions address into the URL bar of your browser and proceed from there.
• Never connect to public Wi-Fi routers directly if possible. You can use a Virtual Private Network (VPN), or you can use a browser plug-in such as HTTPS Everywhere or ForceTLS.
• Since MITB attacks primarily use malware for execution, you should have a comprehensive Internet security solution such as Norton Security installed on your computer, and be sure to keep the program up to date.
• Be sure that your home network is secured. Change all of the default usernames and passwords on your home router and any other equipment.
Source: Norton
Comments






