CryptoWall 4.0 Encrypts Both Files and File Names
Posted by: Timothy Weaver on 11/06/2015 10:14 AM
[
 Comments
]
Comments
]
BleepingComputer.com's editor Lawrence Abrams has reported on a new strain of Cryptowall, the ransomware trojan.
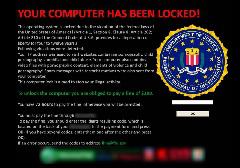 The new version is more powerful than before and poses a security threat that at present has no resolution. Abrams became aware of the new Cryptowall variant when looking into cases where people reported they had been infected by what was called the help_your_files ransomware. He quickly determined that this was in fact a new version of CryptoWall.
The new version is more powerful than before and poses a security threat that at present has no resolution. Abrams became aware of the new Cryptowall variant when looking into cases where people reported they had been infected by what was called the help_your_files ransomware. He quickly determined that this was in fact a new version of CryptoWall.
This new version not only encrypts your files, but also encrypts the file names, thereby making it even more difficult to know which files need to be replaced.
CryptoWall continues to be distributed by emails. The attachment that carries the payload is usually a CV file. Once clicked on, the file downloads a collection of JavaScript files that when executed would download an executable, save it to the Windows %Temp% folder, and then execute it.
Once it becomes active, CrytoWall will inject itself into Explorer.exe and disable System Restore, delete all Shadow Volume copies, and use bcdedit to turn off Windows Startup Repair. Once that is done, it injects itself into the Svchost file and starts encrypting all files on all drives. It then pops up the ransom note.
At present, there is no way to recover files without restoring from a backup or paying the ransom.
Source: SCMagazine
 The new version is more powerful than before and poses a security threat that at present has no resolution. Abrams became aware of the new Cryptowall variant when looking into cases where people reported they had been infected by what was called the help_your_files ransomware. He quickly determined that this was in fact a new version of CryptoWall.
The new version is more powerful than before and poses a security threat that at present has no resolution. Abrams became aware of the new Cryptowall variant when looking into cases where people reported they had been infected by what was called the help_your_files ransomware. He quickly determined that this was in fact a new version of CryptoWall. This new version not only encrypts your files, but also encrypts the file names, thereby making it even more difficult to know which files need to be replaced.
CryptoWall continues to be distributed by emails. The attachment that carries the payload is usually a CV file. Once clicked on, the file downloads a collection of JavaScript files that when executed would download an executable, save it to the Windows %Temp% folder, and then execute it.
Once it becomes active, CrytoWall will inject itself into Explorer.exe and disable System Restore, delete all Shadow Volume copies, and use bcdedit to turn off Windows Startup Repair. Once that is done, it injects itself into the Svchost file and starts encrypting all files on all drives. It then pops up the ransom note.
At present, there is no way to recover files without restoring from a backup or paying the ransom.
Source: SCMagazine
Comments






