CTB-Locker Now Targets Websites
Posted by: Timothy Weaver on 03/03/2016 11:15 AM
[
 Comments
]
Comments
]
A new variant of Crypto ransomware CTB-Locker now targets websites instead of Windows.
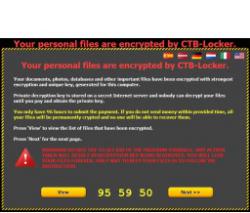 According to PC World, at least 102 websites have been infected since the campaign began on 12 February. The first indication was when the British Association for Counselling and Psychotherapy website fell victim to the attack.
According to PC World, at least 102 websites have been infected since the campaign began on 12 February. The first indication was when the British Association for Counselling and Psychotherapy website fell victim to the attack.
As with most ransomware, the PHP-written program encrypts all the files in the server's web directory. All it takes is a specifically crafted request from an attacker. The hackers are being helpful in that they offer to chat with the victims to help them with paying the ransom of 0.8 bitcoin.
Benkow, a security analyst from Stormshield, is unsure how the attackers gained access to the website. He has ruled out vulnerabilities in a content management system (CMS) such as WordPress since some of the affected sites did not use a CMS.
Benkow said, “The infected hosts run both Linux and Windows and the majority of them (73 percent) host an Exim service (SMTP server). Some of them are vulnerable to ShellShock, but without a deep access on victims' servers, it is difficult to understand how this ransomware infected hosts.”
The campaign is still active.
Source: SCMagazine
 According to PC World, at least 102 websites have been infected since the campaign began on 12 February. The first indication was when the British Association for Counselling and Psychotherapy website fell victim to the attack.
According to PC World, at least 102 websites have been infected since the campaign began on 12 February. The first indication was when the British Association for Counselling and Psychotherapy website fell victim to the attack. As with most ransomware, the PHP-written program encrypts all the files in the server's web directory. All it takes is a specifically crafted request from an attacker. The hackers are being helpful in that they offer to chat with the victims to help them with paying the ransom of 0.8 bitcoin.
Benkow, a security analyst from Stormshield, is unsure how the attackers gained access to the website. He has ruled out vulnerabilities in a content management system (CMS) such as WordPress since some of the affected sites did not use a CMS.
Benkow said, “The infected hosts run both Linux and Windows and the majority of them (73 percent) host an Exim service (SMTP server). Some of them are vulnerable to ShellShock, but without a deep access on victims' servers, it is difficult to understand how this ransomware infected hosts.”
The campaign is still active.
Source: SCMagazine
Comments





