Dropbox: We were not hacked, third party services compromised
Posted by: Jon Ben-Mayor on 10/14/2014 05:46 AM
[
 Comments
]
Comments
]
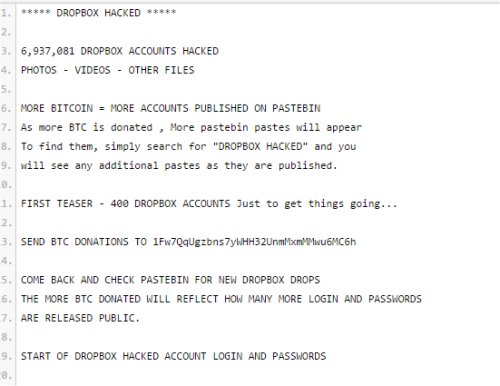
A Bitcoin cyber ransom is being sought for the release of alleged Dropbox usernames and passwords on Pastebin; the unsavory user claims to have hacked over 6,937,081 accounts. The user released 400 "just to get things going..."
Dropbox was quick to discredit the claim on their blog - Recent news articles claiming that Dropbox was hacked aren’t true. Your stuff is safe. The usernames and passwords referenced in these articles were stolen from unrelated services, not Dropbox. Attackers then used these stolen credentials to try to log in to sites across the internet, including Dropbox. We have measures in place to detect suspicious login activity and we automatically reset passwords when it happens.
Attacks like these are one of the reasons why we strongly encourage users not to reuse passwords across services. For an added layer of security, we always recommend enabling 2 step verification on your account.

Update: 10/14/2014 12:30am PT
A subsequent list of usernames and passwords has been posted online. We’ve checked and these are not associated with Dropbox accounts.
It’s unclear exactly which other website(s) or service(s) is the source of the security breach. But Dropbox’s statement confirms the initially posted credentials are — or rather were — genuine account logins for its service. Albeit now reset. It also says no actual accounts were compromised as a result of the leaked credentials, according to Tech Crunch.
If it’s a case of simple password cross pollination (i.e. web users reusing the same login credentials) across multiple services then Dropbox’s claim that its servers have not been hacked does technically stand up. However the end result — user accounts compromised — is the same.

Dropbox was quick to discredit the claim on their blog - Recent news articles claiming that Dropbox was hacked aren’t true. Your stuff is safe. The usernames and passwords referenced in these articles were stolen from unrelated services, not Dropbox. Attackers then used these stolen credentials to try to log in to sites across the internet, including Dropbox. We have measures in place to detect suspicious login activity and we automatically reset passwords when it happens.
Attacks like these are one of the reasons why we strongly encourage users not to reuse passwords across services. For an added layer of security, we always recommend enabling 2 step verification on your account.

Update: 10/14/2014 12:30am PT
A subsequent list of usernames and passwords has been posted online. We’ve checked and these are not associated with Dropbox accounts.
It’s unclear exactly which other website(s) or service(s) is the source of the security breach. But Dropbox’s statement confirms the initially posted credentials are — or rather were — genuine account logins for its service. Albeit now reset. It also says no actual accounts were compromised as a result of the leaked credentials, according to Tech Crunch.
If it’s a case of simple password cross pollination (i.e. web users reusing the same login credentials) across multiple services then Dropbox’s claim that its servers have not been hacked does technically stand up. However the end result — user accounts compromised — is the same.
Comments






