Dyre Banking Trojan Strikes Again
Posted by: Timothy Weaver on 07/13/2015 09:27 AM
[
 Comments
]
Comments
]
Another attack by the Dyre banking trojan is making the rounds.
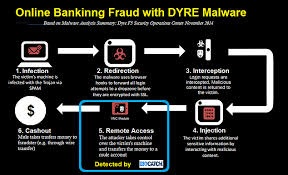 Victims are sent a spam email that has a malicious attachment. It claims to come from a tax consultant. The message asks users to urgently download the attached archive and provide information to complete a financial transaction.
Victims are sent a spam email that has a malicious attachment. It claims to come from a tax consultant. The message asks users to urgently download the attached archive and provide information to complete a financial transaction.
The attachment is an exe file that acts as a downloader which fetches and executes the Dyreza banker Trojan, also known as Dyre.
Dyre is very sneaky as it lays dormant until the victim attempts to log into their banking account. Through a man-in-the-browser attack, Hackers inject malicious Javascript code through a man-in-the-browser attack, allowing them to steal credentials and further manipulate accounts– all completely covertly.
It targets different banks in different countries. In the U.S., clients are Bank of America, Citibank, Wells Fargo, JP Morgan Chase and PayPal.
19,000 malicious emails were sent in three days from spam servers in the US, Taiwan, Hong Kong, Denmark, Russia, China, South Korea, UK, Australia and several other areas.
Source: HotforSecurity
 Victims are sent a spam email that has a malicious attachment. It claims to come from a tax consultant. The message asks users to urgently download the attached archive and provide information to complete a financial transaction.
Victims are sent a spam email that has a malicious attachment. It claims to come from a tax consultant. The message asks users to urgently download the attached archive and provide information to complete a financial transaction. The attachment is an exe file that acts as a downloader which fetches and executes the Dyreza banker Trojan, also known as Dyre.
Dyre is very sneaky as it lays dormant until the victim attempts to log into their banking account. Through a man-in-the-browser attack, Hackers inject malicious Javascript code through a man-in-the-browser attack, allowing them to steal credentials and further manipulate accounts– all completely covertly.
It targets different banks in different countries. In the U.S., clients are Bank of America, Citibank, Wells Fargo, JP Morgan Chase and PayPal.
19,000 malicious emails were sent in three days from spam servers in the US, Taiwan, Hong Kong, Denmark, Russia, China, South Korea, UK, Australia and several other areas.
Source: HotforSecurity
Comments






