FBI and CISA Issue Bl00dy Ransomware Warning for Papercut Admins
Posted by: Corporal Punishment on 05/13/2023 09:35 AM
[
 Comments
]
Comments
]
The FBI and CISA (Cybersecurity and Infrastructure Security Agency)have issued a joint advisory to warn about the Bl00dy Ransomware attacks and urge PaperCut users to apply the latest security updates.
This exploit, being propagated by the Bl00dy Ransomware Gang, allows an unauthenticated user to execute malicious code remotely without credentials and, in this case, encrypt files for ransom. The Bl00dy Ransomware Gang targets organizations using double extortion techniques. It encrypts files on the victim's machine and appends the extension of encrypted files as ".DRTTY." They then steal the data and threaten to publish or sell it if the ransom is not paid.
This version of the exploit has been targeting education facilities, where many PaperCut servers are exposed to the internet.
That's evil, but the irony isn't lost on me. I mean, institutions that make you pay for education, are being exported to pay for the education of patching their software. The only question is which is more expensive, the tuition or the extortion?
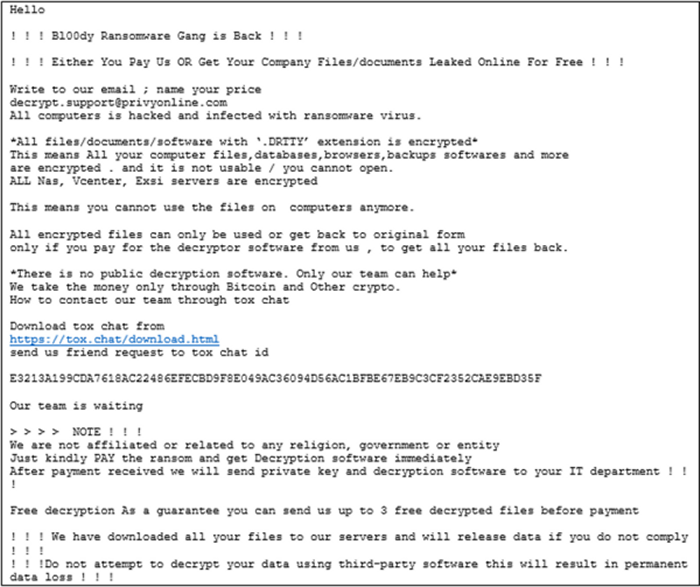
This exploit, being propagated by the Bl00dy Ransomware Gang, allows an unauthenticated user to execute malicious code remotely without credentials and, in this case, encrypt files for ransom. The Bl00dy Ransomware Gang targets organizations using double extortion techniques. It encrypts files on the victim's machine and appends the extension of encrypted files as ".DRTTY." They then steal the data and threaten to publish or sell it if the ransom is not paid.
This version of the exploit has been targeting education facilities, where many PaperCut servers are exposed to the internet.
That's evil, but the irony isn't lost on me. I mean, institutions that make you pay for education, are being exported to pay for the education of patching their software. The only question is which is more expensive, the tuition or the extortion?

Comments






