How hackers infiltrate a system and remain undetected
Posted by: Timothy Weaver on 01/26/2015 10:04 AM
[
 Comments
]
Comments
]
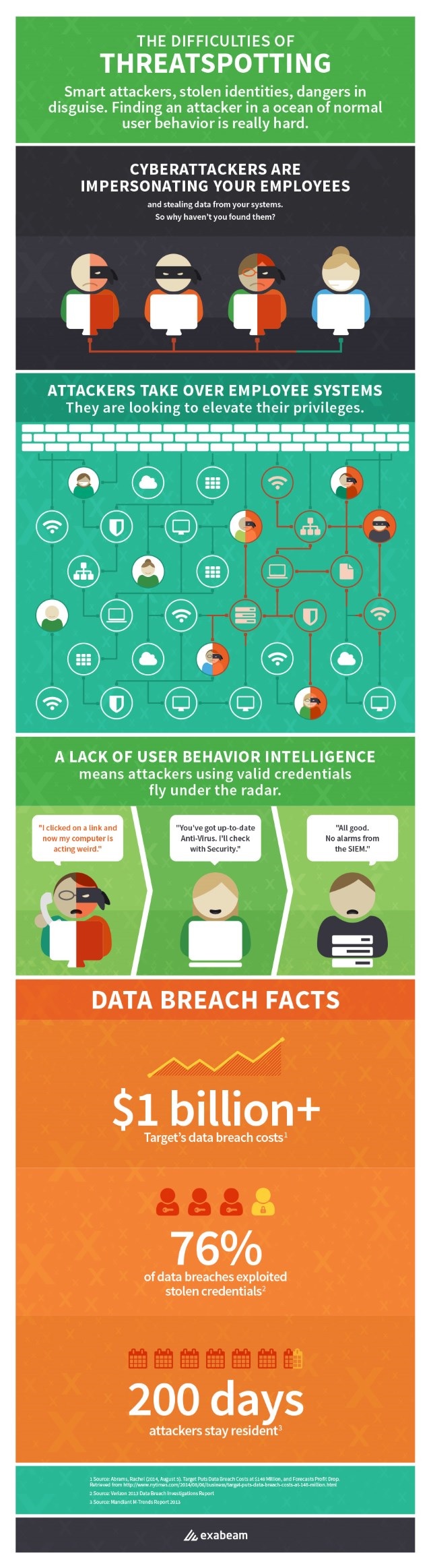
Big data security specialist Exabeam has produced an infographic showing how hackers can penetrate a network and remain difficult to spot.

Comments






