How to Avoid and Deal With Cryptowall and Ransomware
Posted by: Timothy Tibbetts on 11/06/2015 06:39 AM
[
 Comments
]
Comments
]
I recently had the misfortune of dealing with one of the worst malware infections to ever come along; CryptoWall. While it has numerous names (Cryptolocker, for example) and variations, we can call it Ransomware for the purpose of this article. Here’s some information on this nasty Trojan.
Ransomware will encrypt files on your hard drive making them inaccessible. If you’ve never used an encryption program before, it lets you lock any file or folder so only you can access it with a password you choose. So, as you can imagine, if someone locks a file or folder on YOUR computer and you don’t have the password, you’re screwed. This is where this Trojan demands a ransom to unlock your files. So far it is believed that Ransomware has netted these thieves hundreds of millions of dollars (325 million at the time of this article).
What does it look like?
While it might vary a little you can usually expect to see as many as 3-4 text files and graphics similar to this:
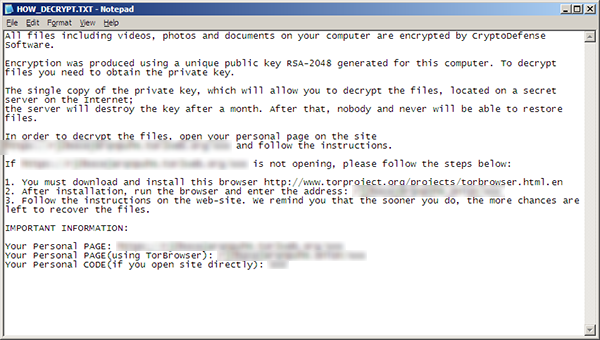
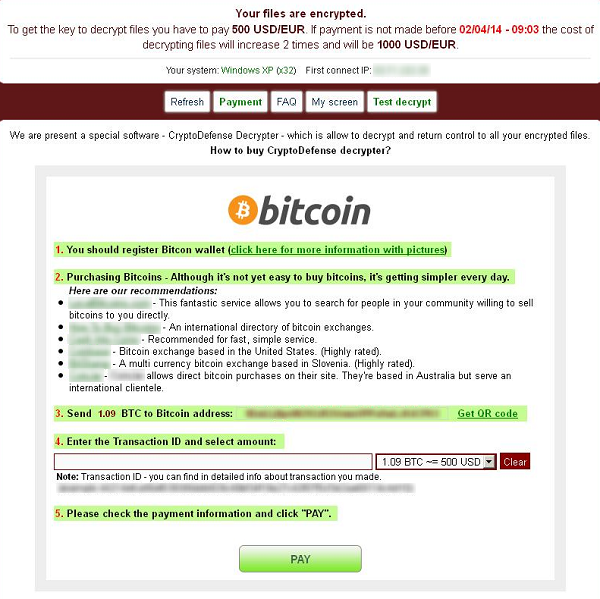
How did you get it?
Odds are you got it from a spam email, a malicious ad or a compromised website.
How do you avoid it?
Don’t open email attachments. Don’t click on links in emails. Don’t go to websites you don’t recognize. Use bookmarks to go to your favorite websites. Mistyping a website name could easily take you to a website that is setup just waiting for people like you to make a typing error. Backup your computer. I like to use multiple backups. I have a second hard drive, an external hard drive and I create occasional CD or DVD’s. You might also consider using cloud storage as well, something that didn’t exist years ago and simplifies backing up for the average user.
How do you clean it out?
Long story short; you don’t. You would have to find a way to decrypt the actual file that is running first. On a recent attempt I had 316 malicious files on the hard drive. They were all .PNG and HTML (web pages) scattered in every directory, even my anti-virus folders. Every time you delete one of these files it is recreated in the same place and often times in new locations. Unless you can decrypt and delete the file (an executeable, process or service) you can’t stop it. Because I like a challenge I threw everything and the kitchen sink at this. Malwarebytes wouldn’t update its definitions and got stuck right there, IObit Malware Fighter and SuperAntispyware didn’t see it and many other niche tools like ADWCleaner and more simply did nothing. Malwarebytes Anti-Rootkit actually found the 4 files that were hidden in a startup folder and removed them. That managed to stop loading the files from appearing on startup so that the computer I worked was easier to use but that’s about the best you’re going to do.
I knew I was in trouble when I felt I went as far as I could and called one of our Support Forum malware team to see if he had any ideas. When one of best anti-malware teams in the country responds with "oh sh*t" you know you're in trouble.
So your best bet here is to restore your computer to factory settings. This deletes your hard drive completely and restores your computer to brand new.
How to restore my computer?
If you backup regularly then you don't need to worry because your files are safe somewhere else, right? Many people HAD to pay the ransom because important files were encrypted and they had to have them back. Don't be that person. Here's more on that...
Backup any files you need that aren't encrypted. If you don’t know how to restore simply Google your computer name and something like factory reset key to find out what key you need to press on reboot to restore. So if you own a Toshiba type in “Toshiba factory reset key”. Some computers have the factory restore built into your control panel or in your applications. For example, Start, Dell, Recovery or something similar.
How to protect yourself from this in the future?
Now that you’re back to factory settings you’re someone who needs to be concerned it could happen again. I recommend Acronis True Image to make a copy of your drive. It can also create checkpoints so you can roll back at any time. It will cost you around $50 bucks but it's cheaper than any ransom you might run across. If money is an issue at least be sure to use some sort of backup or consider a free imaging program like Macrium Reflect.
You might also consider downloading Bitdefender Anti-Ransomware. Bitdefender is a top name in anti-virus and anti-malware and one of my favorite anti-virus programs. This tool is free and only uses about 8 MB of memory. It won’t protect against all variants, but can protect against many. At the time of this article this includes the first 2 variants.
Update: Since this story was written Kaspersky released the CoinVaultDecryptor Tool. CoinVaultDecryptor is a ransomware solution that provides specific data that will help you decrypt the files being held hostage on your PC from the Coinvault and Bitcryptor ransomware. Download it at http://www.majorgeeks.com/files/details/kaspersky_coinvaultdecryptor_tool.html
Ransomware will encrypt files on your hard drive making them inaccessible. If you’ve never used an encryption program before, it lets you lock any file or folder so only you can access it with a password you choose. So, as you can imagine, if someone locks a file or folder on YOUR computer and you don’t have the password, you’re screwed. This is where this Trojan demands a ransom to unlock your files. So far it is believed that Ransomware has netted these thieves hundreds of millions of dollars (325 million at the time of this article).
What does it look like?
While it might vary a little you can usually expect to see as many as 3-4 text files and graphics similar to this:


How did you get it?
Odds are you got it from a spam email, a malicious ad or a compromised website.
How do you avoid it?
Don’t open email attachments. Don’t click on links in emails. Don’t go to websites you don’t recognize. Use bookmarks to go to your favorite websites. Mistyping a website name could easily take you to a website that is setup just waiting for people like you to make a typing error. Backup your computer. I like to use multiple backups. I have a second hard drive, an external hard drive and I create occasional CD or DVD’s. You might also consider using cloud storage as well, something that didn’t exist years ago and simplifies backing up for the average user.
How do you clean it out?
Long story short; you don’t. You would have to find a way to decrypt the actual file that is running first. On a recent attempt I had 316 malicious files on the hard drive. They were all .PNG and HTML (web pages) scattered in every directory, even my anti-virus folders. Every time you delete one of these files it is recreated in the same place and often times in new locations. Unless you can decrypt and delete the file (an executeable, process or service) you can’t stop it. Because I like a challenge I threw everything and the kitchen sink at this. Malwarebytes wouldn’t update its definitions and got stuck right there, IObit Malware Fighter and SuperAntispyware didn’t see it and many other niche tools like ADWCleaner and more simply did nothing. Malwarebytes Anti-Rootkit actually found the 4 files that were hidden in a startup folder and removed them. That managed to stop loading the files from appearing on startup so that the computer I worked was easier to use but that’s about the best you’re going to do.
I knew I was in trouble when I felt I went as far as I could and called one of our Support Forum malware team to see if he had any ideas. When one of best anti-malware teams in the country responds with "oh sh*t" you know you're in trouble.
So your best bet here is to restore your computer to factory settings. This deletes your hard drive completely and restores your computer to brand new.
How to restore my computer?
If you backup regularly then you don't need to worry because your files are safe somewhere else, right? Many people HAD to pay the ransom because important files were encrypted and they had to have them back. Don't be that person. Here's more on that...
Backup any files you need that aren't encrypted. If you don’t know how to restore simply Google your computer name and something like factory reset key to find out what key you need to press on reboot to restore. So if you own a Toshiba type in “Toshiba factory reset key”. Some computers have the factory restore built into your control panel or in your applications. For example, Start, Dell, Recovery or something similar.
How to protect yourself from this in the future?
Now that you’re back to factory settings you’re someone who needs to be concerned it could happen again. I recommend Acronis True Image to make a copy of your drive. It can also create checkpoints so you can roll back at any time. It will cost you around $50 bucks but it's cheaper than any ransom you might run across. If money is an issue at least be sure to use some sort of backup or consider a free imaging program like Macrium Reflect.
You might also consider downloading Bitdefender Anti-Ransomware. Bitdefender is a top name in anti-virus and anti-malware and one of my favorite anti-virus programs. This tool is free and only uses about 8 MB of memory. It won’t protect against all variants, but can protect against many. At the time of this article this includes the first 2 variants.
Update: Since this story was written Kaspersky released the CoinVaultDecryptor Tool. CoinVaultDecryptor is a ransomware solution that provides specific data that will help you decrypt the files being held hostage on your PC from the Coinvault and Bitcryptor ransomware. Download it at http://www.majorgeeks.com/files/details/kaspersky_coinvaultdecryptor_tool.html
Comments





