Java Back Door Acts as Bot (VIDEO)
Posted by: Timothy Tibbetts on 08/02/2013 06:45 AM
[
 Comments
]
Comments
]
The current threat landscape is often driven by web-based malware and exploit kits that are regularly updated with newly found vulnerabilities. Recently, McAfee received an interesting malware binary–a JAR package that opens a back door for an attacker to execute commands and acts as a bot after infection.
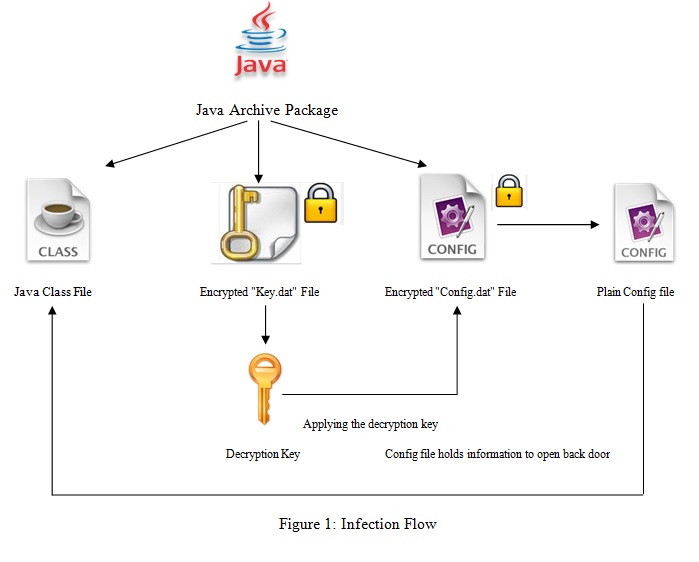
McAfee, and most modern anti-virus or anti-malware programs detect all malicious JAR packages related to this threat as JV/BackDoor-FAZY. It is always good practice to scan any email attachment with an up-to-date antimalware product.
Here is a simple demonstration of how this malware binary can be used by an attacker to execute commands on an infected system:

McAfee, and most modern anti-virus or anti-malware programs detect all malicious JAR packages related to this threat as JV/BackDoor-FAZY. It is always good practice to scan any email attachment with an up-to-date antimalware product.
Here is a simple demonstration of how this malware binary can be used by an attacker to execute commands on an infected system:
Comments





