Malware Authors Employ Variety to Evade Security Detection
Posted by: Timothy Tibbetts on 09/02/2013 07:52 AM
[
 Comments
]
Comments
]
In Arvind Gowda's blog at McAfeee he discussed procedure prologue and procedure epilogue techniques to evade security systems. They now have come across one more set of fake-alert samples that use a different technique to evade detection.
Dynamic Loading
Dynamic loading is a mechanism by which a program loads a library into memory at runtime so that the addresses of the functions and variables contained in the library can be executed or accessed. Dynamic loading is done using an API LoadLibrary, which takes a string argument (the name of the library to be loaded).
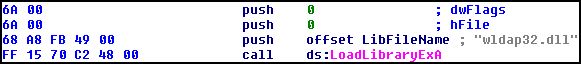
The following screenshot is a typical LoadLibrary code with argument.
Malware authors are always searching for new techniques to evade detection, but eventually their techniques are discovered and blocked by security researchers. McAfee detects all the variants that use these techniques.
Dynamic Loading
Dynamic loading is a mechanism by which a program loads a library into memory at runtime so that the addresses of the functions and variables contained in the library can be executed or accessed. Dynamic loading is done using an API LoadLibrary, which takes a string argument (the name of the library to be loaded).
The following screenshot is a typical LoadLibrary code with argument.

Malware authors are always searching for new techniques to evade detection, but eventually their techniques are discovered and blocked by security researchers. McAfee detects all the variants that use these techniques.
Comments






