Malware hiding in cloud
Posted by: Timothy Weaver on 07/17/2014 03:04 PM
[
 Comments
]
Comments
]
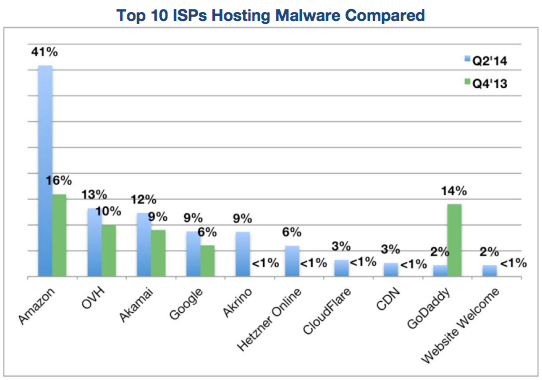
According to NTT subsidiary Solutionary, Amazon Web Service is the top ISP hosting malware. Solutionary posted the top 10 ISP's and their share of malware for both the Q4 2013 to Q2 2014. This is not new as Kaspersky researchers discovered in 2011 that Amazon Web Services was playing host to the notorious SpyEye malware.
"When you start going into the underground forums – the Russian forums, the Chinese forums – they don't just sell a Zeus malware package, they'll sell you an entire command-and-control infrastructure and a phishing website to set up, and a drive-by-download website to set up. You go to them and it's crime-as-a-service," he explained. "It's truly script kiddies on a major scale."
Large providers have a difficult time because the criminals are flitting rapidly between different clouds.
Kahl said: "A lot of the malware operators bounce in between hosting providers, internet service providers and proxy hosts in different countries."
As for Amazon, a spokesperson told us: "AWS employs a number of mitigation techniques, both manual and automated, to prevent the misuse of the services.

"When you start going into the underground forums – the Russian forums, the Chinese forums – they don't just sell a Zeus malware package, they'll sell you an entire command-and-control infrastructure and a phishing website to set up, and a drive-by-download website to set up. You go to them and it's crime-as-a-service," he explained. "It's truly script kiddies on a major scale."
Large providers have a difficult time because the criminals are flitting rapidly between different clouds.
Kahl said: "A lot of the malware operators bounce in between hosting providers, internet service providers and proxy hosts in different countries."
As for Amazon, a spokesperson told us: "AWS employs a number of mitigation techniques, both manual and automated, to prevent the misuse of the services.
Comments






