Massive Spam Attack Delivers Locky Ransomware
Posted by: Timothy Weaver on 03/15/2016 11:09 AM
[
 Comments
]
Comments
]
Security firm Trustwave is reporting a huge uptick in the spam attack that is spreading the Locky ransomware through an infected Java Script attachment.
The intense spam campaigns signal a new attack strategy for those behind Locky ransomware. Rodel Mendrez, a security researcher with Trustwave, said: "The sheer volume and high influx of Locky ransomware spam over the past weeks is what makes it noteworthy.”
“The actors behind the campaigns have merely changed the delivery mechanism (.js attachment) and the end malware – ransomware,” wrote Mendrez in a security bulletin posted to the company’s SpiderLabs research blog. “It’s the same botnet, different day, and different payload,” Mendrez wrote.
Locky is not taking advantage of any vulnerability, but is instead relying on social engineering. Mendrez said. “It uses social engineering and takes advantage of human gullibility to infect systems. Even the up-to-date systems are not protected.”
Trustwave recommends admin bolster their spam defenses by blocking the Locky spam attacks at the email gateway by filtering out inbound email with .js attachments and Office documents with macros.
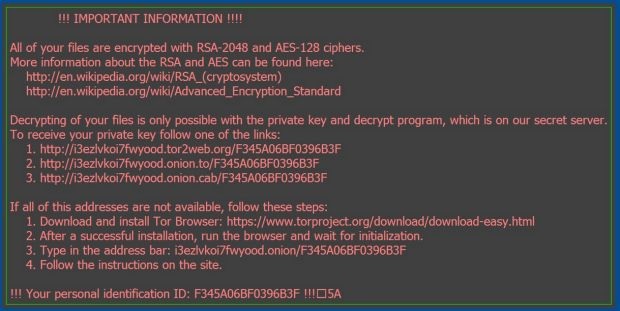
Source: ThreatPost
The intense spam campaigns signal a new attack strategy for those behind Locky ransomware. Rodel Mendrez, a security researcher with Trustwave, said: "The sheer volume and high influx of Locky ransomware spam over the past weeks is what makes it noteworthy.”
“The actors behind the campaigns have merely changed the delivery mechanism (.js attachment) and the end malware – ransomware,” wrote Mendrez in a security bulletin posted to the company’s SpiderLabs research blog. “It’s the same botnet, different day, and different payload,” Mendrez wrote.
Locky is not taking advantage of any vulnerability, but is instead relying on social engineering. Mendrez said. “It uses social engineering and takes advantage of human gullibility to infect systems. Even the up-to-date systems are not protected.”
Trustwave recommends admin bolster their spam defenses by blocking the Locky spam attacks at the email gateway by filtering out inbound email with .js attachments and Office documents with macros.

Source: ThreatPost
Comments





