New Tool to Decrypt Jigsaw Ransomware
Posted by: Timothy Weaver on 07/15/2016 12:38 PM
[
 Comments
]
Comments
]
Researchers have found a way to bypass the payment for Jigsaw ransomware.
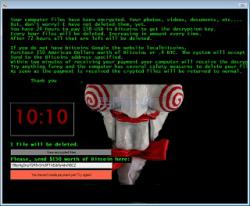 While researching the source code, they found that when pressing the button "I made my payment now where are my files", the code is this:
While researching the source code, they found that when pressing the button "I made my payment now where are my files", the code is this:
json: {“status”:”success”,”data”:{“address”:””,”balance”:0,”balance_multisig”:0},”code”:200,”message”:””}
So they changed the response variable from 0 to 10. To their delight, Jigsaw interpreted this change as receipt of payment and began decrypting the files!
This trick also works on older versions of Jigsaw and not only decrypts the files but leaves no traces of the malware on the victims system.
Check Point has built a decryption tool that incorporates this latest trick. It is freely available for download here.
Source: Graham Cluley
 While researching the source code, they found that when pressing the button "I made my payment now where are my files", the code is this:
While researching the source code, they found that when pressing the button "I made my payment now where are my files", the code is this:json: {“status”:”success”,”data”:{“address”:””,”balance”:0,”balance_multisig”:0},”code”:200,”message”:””}
So they changed the response variable from 0 to 10. To their delight, Jigsaw interpreted this change as receipt of payment and began decrypting the files!
This trick also works on older versions of Jigsaw and not only decrypts the files but leaves no traces of the malware on the victims system.
Check Point has built a decryption tool that incorporates this latest trick. It is freely available for download here.
Source: Graham Cluley
Comments






