Phishing scam targets Google Docs users
Posted by: Jon Ben-Mayor on 03/18/2014 08:21 AM
[
 Comments
]
Comments
]
Scammers have been attempting to use Google Docs and Google Drive to target users; this phishing attack comes as a simple email with "Documents" in the subject line. It requests that the recipient view the important document via the included link. This type of request should always send off warning bells.
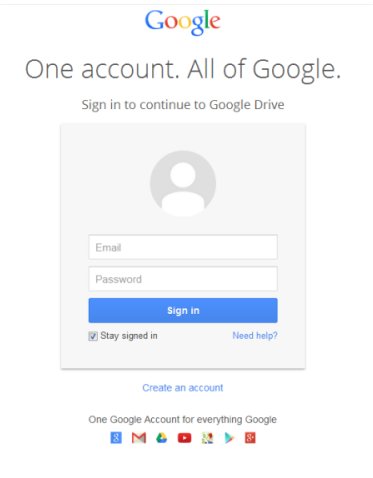
The fact that it does go to Google - makes it a bit harder to immediately decipher that it is actually a scam. The fake page is hosted on Google's servers and is served over SSL, making the page even more convincing.
According to Symantec, the scammers have simply created a folder inside a Google Drive account, marked it as public, uploaded a file there, and then used Google Drive's preview feature to get a publicly-accessible URL to include in their messages.
This login page will look familiar to many Google users, as it's used across Google's services. (The text below "One account. All of Google." mentions what service is being accessed, but this is a subtlety that many will not notice.)
After pressing "Sign in", the user’s credentials are sent to a PHP script on a compromised web server.
This page then redirects to a real Google Docs document, making the whole attack very convincing.
Remember that an unsolicited email that asks you to click around should always be considered suspect (regardless of where it came from). Best bet is to enter the address into your browser's address bar rather than clicking on an unsolicited link.

The fact that it does go to Google - makes it a bit harder to immediately decipher that it is actually a scam. The fake page is hosted on Google's servers and is served over SSL, making the page even more convincing.
According to Symantec, the scammers have simply created a folder inside a Google Drive account, marked it as public, uploaded a file there, and then used Google Drive's preview feature to get a publicly-accessible URL to include in their messages.
This login page will look familiar to many Google users, as it's used across Google's services. (The text below "One account. All of Google." mentions what service is being accessed, but this is a subtlety that many will not notice.)
After pressing "Sign in", the user’s credentials are sent to a PHP script on a compromised web server.
This page then redirects to a real Google Docs document, making the whole attack very convincing.
Remember that an unsolicited email that asks you to click around should always be considered suspect (regardless of where it came from). Best bet is to enter the address into your browser's address bar rather than clicking on an unsolicited link.
Comments





