Ransomware evolving
Posted by: Timothy Weaver on 02/10/2015 03:02 PM
[
 Comments
]
Comments
]
Ransomware authors are streamlining their malware in the hopes to attack more users.
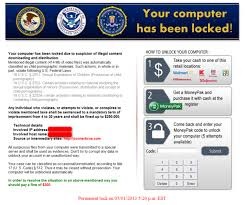
The biggest threat in ransomware is CryptoWall, which encrypts a wide range of files and demands that victims pay a ransom in Bitcoin cryptocurrency to recover them.
It is proving harder to track down because it uses the Tor and I2P anonymity networks. According to Cisco Systems, the latest version, CryptoWall 3.0, was launched in January after a two-month break by its creators. One notable change: it no longer bundles local privilege escalation exploits.
Privilege escalation exploits allow attackers to execute malware programs with administrator or system-level privileges instead of using the victim’s local user account, which might be restricted.
And it appears as though the malware authors plan to rely more on Web-based drive-by download attacks to infect systems. Drive-by download attacks are launched from compromised websites or through malicious ads and usually exploit vulnerabilities in browser plug-ins like Flash Player, Java, Adobe Reader or Silverlight. However, this does not mean they have abandoned email methods.
F-Secure reported Monday that they’ve observed a significant increase this month in infections with another file-encrypting ransomware program called CTB-Locker. CTB-Locker is most commonly spread through emails with a malicious zip file attachment.
“The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices,” Avast researcher Nikolaos Chrysaidos said in a blog post Tuesday.
Security researchers advise against paying such ransoms to cybercriminals, because there’s no guarantee of getting the decryption key and because it encourages them to continue their scheme.
Files should be backed up to drives or network shares that are only temporarily connected to the computer or that require a username and password to be accessed. That’s because ransomware programs will also encrypt files from folders accessible over the network if they can write to them.

The biggest threat in ransomware is CryptoWall, which encrypts a wide range of files and demands that victims pay a ransom in Bitcoin cryptocurrency to recover them.
It is proving harder to track down because it uses the Tor and I2P anonymity networks. According to Cisco Systems, the latest version, CryptoWall 3.0, was launched in January after a two-month break by its creators. One notable change: it no longer bundles local privilege escalation exploits.
Privilege escalation exploits allow attackers to execute malware programs with administrator or system-level privileges instead of using the victim’s local user account, which might be restricted.
And it appears as though the malware authors plan to rely more on Web-based drive-by download attacks to infect systems. Drive-by download attacks are launched from compromised websites or through malicious ads and usually exploit vulnerabilities in browser plug-ins like Flash Player, Java, Adobe Reader or Silverlight. However, this does not mean they have abandoned email methods.
F-Secure reported Monday that they’ve observed a significant increase this month in infections with another file-encrypting ransomware program called CTB-Locker. CTB-Locker is most commonly spread through emails with a malicious zip file attachment.
“The reason why this variant is more dangerous than its predecessor is that it generates unique keys for each infected device, making it harder to decrypt infected devices,” Avast researcher Nikolaos Chrysaidos said in a blog post Tuesday.
Security researchers advise against paying such ransoms to cybercriminals, because there’s no guarantee of getting the decryption key and because it encourages them to continue their scheme.
Files should be backed up to drives or network shares that are only temporarily connected to the computer or that require a username and password to be accessed. That’s because ransomware programs will also encrypt files from folders accessible over the network if they can write to them.
Comments






