Ransomware Now Comes With a DDoS Bot
Posted by: Timothy Weaver on 05/23/2016 10:32 AM
[
 Comments
]
Comments
]
An older piece of ransomware has been reinvented to include DDoS capabilities.
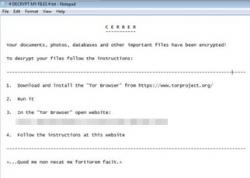 Cerber ransomware, which delivers the ability to lock down your system and encrypt your files, now also sends out a large amount of network traffic from a second binary called 3311.tmp.
Cerber ransomware, which delivers the ability to lock down your system and encrypt your files, now also sends out a large amount of network traffic from a second binary called 3311.tmp.
A sample that was evaluated by Invincea was flagged by 37 out of the 57 antivirus engines on VirusTotal. However, to be successful, the payload documents require the victim to activate the Macro feature in Office which then executes a malicious VBScript that downloads and runs the malware.
Invincea's Ikenna Dike explained: "The observed malware seems to serve multiple purposes. First, it is a typical ransomware binary that encrypts the user’s file system and files while displaying a ransom note. Second, the binary could also be used to carry out a DDoS attack."
"The observed network traffic looks to be flooding the subnet with UDP packets over port 6892. By spoofing the source address, the host could direct all response traffic from the subnet to a targeted host, causing the host to be unresponsive."
If the victim doesn't reformat and reinstall their system, but pays the ransom, it is still possible that the DDoS bot will still be active.
Source: SoftPedia
 Cerber ransomware, which delivers the ability to lock down your system and encrypt your files, now also sends out a large amount of network traffic from a second binary called 3311.tmp.
Cerber ransomware, which delivers the ability to lock down your system and encrypt your files, now also sends out a large amount of network traffic from a second binary called 3311.tmp.A sample that was evaluated by Invincea was flagged by 37 out of the 57 antivirus engines on VirusTotal. However, to be successful, the payload documents require the victim to activate the Macro feature in Office which then executes a malicious VBScript that downloads and runs the malware.
Invincea's Ikenna Dike explained: "The observed malware seems to serve multiple purposes. First, it is a typical ransomware binary that encrypts the user’s file system and files while displaying a ransom note. Second, the binary could also be used to carry out a DDoS attack."
"The observed network traffic looks to be flooding the subnet with UDP packets over port 6892. By spoofing the source address, the host could direct all response traffic from the subnet to a targeted host, causing the host to be unresponsive."
If the victim doesn't reformat and reinstall their system, but pays the ransom, it is still possible that the DDoS bot will still be active.
Source: SoftPedia
Comments






