Researchers identify new GameOver Zeus variant
Posted by: Jon Ben-Mayor on 07/13/2014 07:25 AM
[
 Comments
]
Comments
]
A variant of the GameOver Zeus trojan has been identified by security researchers from Malcovery Security. The new attack is being carried out by a simple spam mail attachment pretending to be from legitimate financial institutions such as NatWest and M&T Bank.
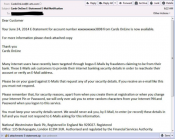
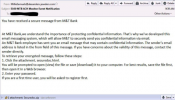 The three spam campaigns each had a .zip attachment. Each of these contained the same file in the form of a “.scr” file with the hash:
The three spam campaigns each had a .zip attachment. Each of these contained the same file in the form of a “.scr” file with the hash:
MD5: 5e5e46145409fb4a5c8a004217eef836
Once the attachment was opened and the malware payload executed, the malware began to make attempts to contact certain websites in accordance with a domain generation algorithm. The goal of these contact attempts is to make contact with a server that can in turn provide instructions to the malware. Many sandboxes would have failed to launch the malware, as the presence of VMWare Tools will stop the malware from executing. Other sandboxes would not have noticed the successful connection, because the malware took between 6 and 10 minutes to randomly generate the single domain name that was used successfully to launch the new Zeus trojan and download the bank information “webinject” files from the server.
Malcovery analysts confirmed with the FBI and Dell Secure Works that the original GameOver Zeus is still "locked down". This new DGA list is not related to the original GameOver Zeus but bears a striking resemblance to the DGA utilized by that trojan.
This discovery indicates that the criminals responsible for GameOver’s distribution do not intend to give up on this botnet even after suffering one of the most expansive botnet takeovers/takedowns in history.

 The three spam campaigns each had a .zip attachment. Each of these contained the same file in the form of a “.scr” file with the hash:
The three spam campaigns each had a .zip attachment. Each of these contained the same file in the form of a “.scr” file with the hash: MD5: 5e5e46145409fb4a5c8a004217eef836
Once the attachment was opened and the malware payload executed, the malware began to make attempts to contact certain websites in accordance with a domain generation algorithm. The goal of these contact attempts is to make contact with a server that can in turn provide instructions to the malware. Many sandboxes would have failed to launch the malware, as the presence of VMWare Tools will stop the malware from executing. Other sandboxes would not have noticed the successful connection, because the malware took between 6 and 10 minutes to randomly generate the single domain name that was used successfully to launch the new Zeus trojan and download the bank information “webinject” files from the server.
Malcovery analysts confirmed with the FBI and Dell Secure Works that the original GameOver Zeus is still "locked down". This new DGA list is not related to the original GameOver Zeus but bears a striking resemblance to the DGA utilized by that trojan.
This discovery indicates that the criminals responsible for GameOver’s distribution do not intend to give up on this botnet even after suffering one of the most expansive botnet takeovers/takedowns in history.
Comments






