RIG Exploit Kit Suffers Severe Blow
Posted by: Timothy Weaver on 06/05/2017 03:19 PM
[
 Comments
]
Comments
]
The RIG Exploit Kit (RIG EK) has suffered a severe blow when a joint operation between various industries got together and shut down and removed thousands of shadow domains.
 The consortium of actors included RSA Research, GoDaddy, Malwarebytes, Brad Duncan, @broadanalysis, @dynamicanalysis, @executemalware, @nao_sec, and @zerophage.
The consortium of actors included RSA Research, GoDaddy, Malwarebytes, Brad Duncan, @broadanalysis, @dynamicanalysis, @executemalware, @nao_sec, and @zerophage.
The target of the group was hundreds of compromised domains secretly hijacked by the RIG EK. Most of the shadow domains were hosted on GoDaddy, which was brought in to contact owners and freeze compromised accounts.
The researchers believe that the sites were compromised by either phishing attacks to gain credentials or brute-force attacks.
In an effort to remain unnoticed, the hackers would rotate domains, creating an average of around 450 shadow domains per day. Further investigation revealed that the hackers took over 800 domains and created around 30,000 shadow domains.
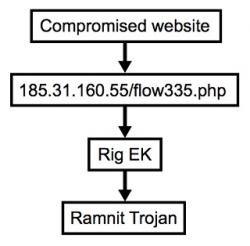
If a victim lands on a compromised site, they get redirected to site after site until they finally land on so-called "landing pages" where the actual RIG exploit kit runs. It then loads malicious code on the victims computer in the form of either a Flash or JavaScript file.
Researchers are hoping that this blow with convince the hackers to call it quits before researchers unmasked more of their infrastructure.
Source: Bleeping Computer
 The consortium of actors included RSA Research, GoDaddy, Malwarebytes, Brad Duncan, @broadanalysis, @dynamicanalysis, @executemalware, @nao_sec, and @zerophage.
The consortium of actors included RSA Research, GoDaddy, Malwarebytes, Brad Duncan, @broadanalysis, @dynamicanalysis, @executemalware, @nao_sec, and @zerophage.The target of the group was hundreds of compromised domains secretly hijacked by the RIG EK. Most of the shadow domains were hosted on GoDaddy, which was brought in to contact owners and freeze compromised accounts.
The researchers believe that the sites were compromised by either phishing attacks to gain credentials or brute-force attacks.
In an effort to remain unnoticed, the hackers would rotate domains, creating an average of around 450 shadow domains per day. Further investigation revealed that the hackers took over 800 domains and created around 30,000 shadow domains.
If a victim lands on a compromised site, they get redirected to site after site until they finally land on so-called "landing pages" where the actual RIG exploit kit runs. It then loads malicious code on the victims computer in the form of either a Flash or JavaScript file.
Researchers are hoping that this blow with convince the hackers to call it quits before researchers unmasked more of their infrastructure.
Source: Bleeping Computer
Comments





