Start-up touts potential end to viruses and malware
Posted by: Jon Ben-Mayor on 02/09/2014 08:53 AM
[
 Comments
]
Comments
]
An Israeli start-up company established about 1 year ago in Beersheba, says that it may have found a way to stop all viruses by going after the "dark heart" of the damaging code that is generally recycled by hackers.
The current cyber security paradigm is a reactive cycle: if and when a threat is exposed, it is analyzed and a counter-solution is designed. Response times vary from weeks to years. Even if a solution is made available, attackers can easily modify the original code, evade the updated security measures, and once again a new threat is born. “Cybersecurity is a never-ending Tom and Jerry cartoon. Like antibiotic-resistant bacteria, attackers adapt to our defenses and render them obsolete” (MIT Tech Review, David Cowan).
According to industry experts, over 98% of malware comprise variants of earlier versions, modified to evade security measures; the remaining 2% use recycled modules, exploits and techniques; even 0-day malware reuse components of previous malware. If writing new malware from scratch is extremely difficult, re-inventing a whole attack chain is practically impossible – and as far as documented attacks are concerned, this has never been done.
The reactive paradigm creates an asymmetric relationship, whereby fighting malware is time-consuming and expensive, while ‘recycling’ malware for reuse is quick and cost effective. The mind-boggling fact is that for every dollar spent by black hat hackers, hundreds of dollars are spent by the IT security industry. This economic imbalance is the springboard from which cyber-crime, cyber-terrorism and cyber-warfare are launched.
The Times of Israel spoke with CEO & Co-Founder, Liran Tancman, who says the secret is that viruses are overwhelmingly evolutionary, not revolutionary. “Much of the code found in even major attacks is reused over and over again in new attacks,”
“There has actually never been a virus that did not draw substantially on malware that was already in existence.”
“If we can develop defenses against the core of the malware, the 98% of the code that is just a variant of existing malware, we could end virus attacks for good,” Tracman said.
Cyactive has developed smart algorithms that Tancman says explore and analyze malware to see where it came from, and where it is going. “You can see very clearly what the ‘keychain of exploitation’ is, the methods hackers are using now and the variants they are likely to use,” said Tancman. “Even the major attacks of recent years, like Flame, Stuxnet, and others, use a similar core.” For hackers, there really is no alternative; they have neither the time, resources, or even skills to build a whole new exploitation keychain that will attack systems from other angles, he claims.
CyActive’s detectors are created in CyActive’s cloud, where they are trained on future attacks forecasted by CyActive’s predictive engine. The detectors are then deployed on the client network (both classic enterprise network and SCADA equipment and embedded devices).
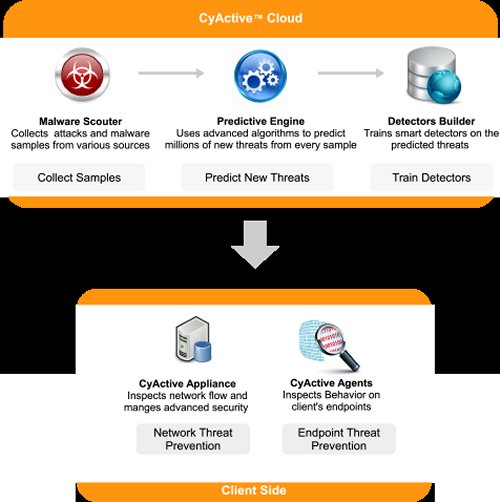
CyActive’s predictive engine automatically forecasts how hackers will evolve today’s malware into tomorrow’s advanced threats, by applying bio-inspired algorithms and a deep understanding of hackers’ behavior, considerations and constraints.
This could be a great development in the fight against malware - hope that they fully succeed!
The current cyber security paradigm is a reactive cycle: if and when a threat is exposed, it is analyzed and a counter-solution is designed. Response times vary from weeks to years. Even if a solution is made available, attackers can easily modify the original code, evade the updated security measures, and once again a new threat is born. “Cybersecurity is a never-ending Tom and Jerry cartoon. Like antibiotic-resistant bacteria, attackers adapt to our defenses and render them obsolete” (MIT Tech Review, David Cowan).
According to industry experts, over 98% of malware comprise variants of earlier versions, modified to evade security measures; the remaining 2% use recycled modules, exploits and techniques; even 0-day malware reuse components of previous malware. If writing new malware from scratch is extremely difficult, re-inventing a whole attack chain is practically impossible – and as far as documented attacks are concerned, this has never been done.
The reactive paradigm creates an asymmetric relationship, whereby fighting malware is time-consuming and expensive, while ‘recycling’ malware for reuse is quick and cost effective. The mind-boggling fact is that for every dollar spent by black hat hackers, hundreds of dollars are spent by the IT security industry. This economic imbalance is the springboard from which cyber-crime, cyber-terrorism and cyber-warfare are launched.
The Times of Israel spoke with CEO & Co-Founder, Liran Tancman, who says the secret is that viruses are overwhelmingly evolutionary, not revolutionary. “Much of the code found in even major attacks is reused over and over again in new attacks,”
“There has actually never been a virus that did not draw substantially on malware that was already in existence.”
“If we can develop defenses against the core of the malware, the 98% of the code that is just a variant of existing malware, we could end virus attacks for good,” Tracman said.
Cyactive has developed smart algorithms that Tancman says explore and analyze malware to see where it came from, and where it is going. “You can see very clearly what the ‘keychain of exploitation’ is, the methods hackers are using now and the variants they are likely to use,” said Tancman. “Even the major attacks of recent years, like Flame, Stuxnet, and others, use a similar core.” For hackers, there really is no alternative; they have neither the time, resources, or even skills to build a whole new exploitation keychain that will attack systems from other angles, he claims.
CyActive’s detectors are created in CyActive’s cloud, where they are trained on future attacks forecasted by CyActive’s predictive engine. The detectors are then deployed on the client network (both classic enterprise network and SCADA equipment and embedded devices).

CyActive’s predictive engine automatically forecasts how hackers will evolve today’s malware into tomorrow’s advanced threats, by applying bio-inspired algorithms and a deep understanding of hackers’ behavior, considerations and constraints.
This could be a great development in the fight against malware - hope that they fully succeed!
Comments






