The FBI Details the Take Down of Avalanche Botnet
Posted by: Timothy Weaver on 07/29/2017 03:25 PM
[
 Comments
]
Comments
]
Tom Grasso, unit chief of the FBI's cyber division, talked about the take down of the Avalanche botnet.
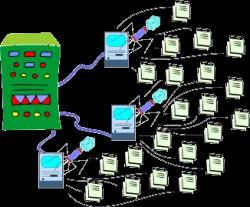 He explained that Avalanche was not a true botnet, but rather an infrastructure for enabling botnets. They served to spread malware campaigns, facilitate "money mule" laundering schemes, and act as a fast-flux communication infrastructure for other botnets.
He explained that Avalanche was not a true botnet, but rather an infrastructure for enabling botnets. They served to spread malware campaigns, facilitate "money mule" laundering schemes, and act as a fast-flux communication infrastructure for other botnets.
This network was responsible for infecting more than 500,000 systems and lead to the loss of millions of dollars. The infrastructure included more than 800,000 malicious domains.
"We're not talking about some kid in his mom's basement; … we're talking about businessmen. This is a business to them," he said. "This was a strategic move by the criminals running this to add another level of complexity to make it unsusceptible to law enforcement intervention."
Grasso explained that the take down was a joint effort by private companies, international organizations and foreign governments. It included FBI agents, German state and federal police, Ukrainian police, Shadowserver, nonprofit Registrar of the Last Resort, and Fraunhofer, a German company that mapped out the technical patterns of Avalanche.
In January 2016, the administrators of Avanlanche moved their server from Moldova to a private server in the US. Authorities got a warrant and searched the server where they found email addresses for the administrators and a buddy list with more than 200 clients.
The investigation resulted in the arrest of five individuals from four countries, the seizure of servers and the ability to sinkhole more than 800,000 malicious domains.
Source: Dark Reading
 He explained that Avalanche was not a true botnet, but rather an infrastructure for enabling botnets. They served to spread malware campaigns, facilitate "money mule" laundering schemes, and act as a fast-flux communication infrastructure for other botnets.
He explained that Avalanche was not a true botnet, but rather an infrastructure for enabling botnets. They served to spread malware campaigns, facilitate "money mule" laundering schemes, and act as a fast-flux communication infrastructure for other botnets.This network was responsible for infecting more than 500,000 systems and lead to the loss of millions of dollars. The infrastructure included more than 800,000 malicious domains.
"We're not talking about some kid in his mom's basement; … we're talking about businessmen. This is a business to them," he said. "This was a strategic move by the criminals running this to add another level of complexity to make it unsusceptible to law enforcement intervention."
Grasso explained that the take down was a joint effort by private companies, international organizations and foreign governments. It included FBI agents, German state and federal police, Ukrainian police, Shadowserver, nonprofit Registrar of the Last Resort, and Fraunhofer, a German company that mapped out the technical patterns of Avalanche.
In January 2016, the administrators of Avanlanche moved their server from Moldova to a private server in the US. Authorities got a warrant and searched the server where they found email addresses for the administrators and a buddy list with more than 200 clients.
The investigation resulted in the arrest of five individuals from four countries, the seizure of servers and the ability to sinkhole more than 800,000 malicious domains.
Source: Dark Reading
Comments






