BitLocker: What Is It and Why Use It?
By Corporal Punishmenton 10/21/2025 |
 BitLocker is Microsoft's built-in encryption tool for Windows, designed to secure data by encrypting entire drives. Bitlocker has been around for a while, since Vista -- believe it or not -- but recently, users have been rediscovering this option, likely because of the requirement of TPM for Win 11, the easier implementation, and the average user's higher privacy/security IQ. We have seen more questions this month on Bitlocker than in the last five years. So what is it and why should you bother?
BitLocker is Microsoft's built-in encryption tool for Windows, designed to secure data by encrypting entire drives. Bitlocker has been around for a while, since Vista -- believe it or not -- but recently, users have been rediscovering this option, likely because of the requirement of TPM for Win 11, the easier implementation, and the average user's higher privacy/security IQ. We have seen more questions this month on Bitlocker than in the last five years. So what is it and why should you bother? Believe it or not, your Windows password or PIN might seem like a solid defense, but it's useless if someone gets their hands on your drive. If you remove a Windows drive and plug it into another machine or boot from a USB, all the files are sitting there, wide open. Your Windows login credentials only protect access to Windows itself. That login doesn't protect the file structure or encrypt your data, which means anyone with basic knowledge can easily bypass them.
Without BitLocker, or something like it, your data is at significant risk if someone physically removes your drive. If a thief takes your hard drive and connects it to another computer, they can easily access all unencrypted files. Encryption is the only real way to prevent unauthorized access in such cases.
BitLocker is a full-disk encryption feature available on Windows Pro and Enterprise editions. It encrypts your data using AES (Advanced Encryption Standard) with 128-bit or 256-bit keys, making it nearly impossible for unauthorized users to access your files without proper authentication. Unlike third-party encryption tools, BitLocker is deeply integrated into Windows, ensuring smooth operation with minimal performance impact (But there is an impact). Since it's built into Windows, there are few compatibility issues with third-party tools. BitLocker works with TPM to provide hardware-based security, preventing attacks targeting the boot process. IT administrators can manage encrypted systems with centralized control, making it easier to enforce security policies. Finally, if a device is lost or stolen, encrypted data remains inaccessible, providing peace of mind.
Bottom line, if you actually want to keep your files safe, you need encryption and BitLocker was designed to do just that. Lock down your drive, making it unreadable without the right key. Without encryption, your Windows "security" is just theater - just for show. So if you are a business looking to protect sensitive files or an individual wanting an extra layer of security, here's what you need to know.
How BitLocker Works with TPM
BitLocker can work with or without a TPM (Trusted Platform Module), but it's most effective when TPM is available. The TPM is a specialized security chip in modern computers that stores encryption keys and verifies system integrity before allowing access to encrypted data. TPM 2.0 availablity is a requirement to install Windows 11. To enable Trusted Platform Module (TPM), you need to do it through your computer's BIOS/UEFI settings. When you enable BitLocker, the encryption keys are stored in the TPM.
At boot-up, the TPM checks if system files and boot components have been tampered with. If everything is intact, BitLocker releases the encryption key and allows normal access. However, if unauthorized modifications are detected, the system locks down and requires a recovery key to proceed.
BitLocker can still function for systems without TPM but will require a USB flash drive with a startup key or a password before the system can boot.
Where to Get BitLocker
BitLocker is included in Windows 10/11 Pro and Enterprise and Windows Server editions. Home users who need BitLocker must upgrade to a Pro version, which can be purchased from Microsoft or licensed retailers.
How to Turn On BitLocker
If your PC has TPM 1.2 or 2.0 enabled, you can enable BitLocker to encrypt your drive and protect your data. The encryption key is stored in TPM, allowing automatic unlocking at boot without requiring a password each time.
Step 1: Check If TPM Is Enabled
Before turning on BitLocker, verify that TPM is available and enabled. Press Win + R, type tpm.msc, and press Enter. Look for "The TPM is ready for use" under Status. If TPM is disabled, reboot your PC and enter BIOS/UEFI to enable it (under Security Settings).
Step 2: Enable BitLocker on Your Drive
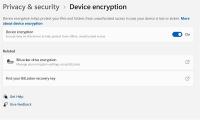
Open Control Panel → Click BitLocker Drive Encryption. (Alternatively, go to: Win + I → Update & Security → Device Encryption (if available).)
Select Turn on BitLocker next to your C: drive. You can add a PIN at startup for extra security, but otherwise, BitLocker will unlock automatically using TPM.
Step 3: Backup Your Recovery Key
You must save your recovery key in case something goes wrong:
Do NOT store the key on the same drive you are encrypting! <<<< re-read that. It happens too often. Don't be that guy/gal.
Step 4: Choose Encryption Type
Step 5: Verify BitLocker is Enabled
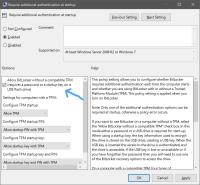
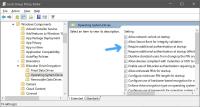
Enable BitLocker Without TPM
If your system lacks a TPM, or you don't want to use it, you can still enable BitLocker by modifying the Group Policy settings. Here's how:
Once this setting is enabled, you can use a password or a USB drive as an authentication method instead of a TPM. Treat that USB stick like Sméagol would the One Ring.
Who Should Use BitLocker?
Anyone who prioritizes data security can benefit from BitLocker. Businesses can use it to protect sensitive corporate data on laptops and desktops. Government agencies and enterprises rely on it to secure classified information. Individuals who want to safeguard personal data from theft or unauthorized access, especially on portable devices, will find it useful. IT administrators also leverage BitLocker to enforce encryption policies and manage recovery keys in an enterprise environment. Specifically, a great use for something like a BitLocker is those with a company laptop that takes information out of the office on a regular basis.
Who Should NOT Use BitLocker or Encryption Software?
While encryption is a strong security measure, it isn't always necessary for everyone. Users who primarily store non-sensitive data on their devices and do not risk the physical loss of their computers might not need encryption.
Those unfamiliar with managing encryption keys may also find BitLocker inconvenient, as losing access to the recovery key can permanently lock data.
Additionally, individuals work in environments where encryption is not required or where performance optimization is a priority, such as gaming PCs or media production workstations. These users should likely avoid BitLocker to avoid impacting their performance.
How Hardware Changes Affect BitLocker
BitLocker is designed to detect hardware changes, as they can be a sign of tampering. If you replace your motherboard, CPU, or TPM chip, BitLocker may consider the system compromised and require your recovery key before allowing access to the drive. Even minor changes, such as upgrading RAM or switching storage devices, may trigger protection. Hell, even sometimes, just looking at your machine the wrong way can trigger BitLocker protection.
To avoid being locked out, it's absolutely crucial to back up your recovery key before making hardware modifications. If you plan on making significant changes, temporarily suspending BitLocker encryption in the settings can help prevent unnecessary lockouts. Once the hardware changes are complete, you can resume BitLocker protection without triggering a security alert.

Storing Your Recovery Key Safely
If you are unsure where your key is you go open the Control Panel and navigate to BitLocker Drive Encryption. Next, back up your recovery key by saving it to your Microsoft account, a USB drive, or a file or printing it out. Then, select your encryption mode. Newer encryption modes are best for fixed drives, while compatible mode works better for removable drives. Finally, click "Start Encrypting" and wait for the process to complete.
Since the recovery key is essential for unlocking your data, if you forget your password or the TPM detects an issue, you need to store it securely. There is no password reset email or guessing your last pets name.. You need that key. The easiest way to back up your key is to save it to your Microsoft account for easy recovery. You can also store it to keep it on a USB drive for offline security, print it out and store it in a safe place, or use a trusted password manager, like Bitwarden or Roboform.
Downsides of BitLocker
While BitLocker is a powerful tool, it does have some downsides. It's only available on Windows Pro and Enterprise editions, meaning Windows Home users are left out. If you lose your recovery key, you lose access to your data. Encryption may cause a slight performance slowdown, particularly on older hardware. Unlike some encryption tools, BitLocker doesn't offer file-level encryption—it encrypts entire drives instead. To get the full benefit of BitLocker, you also need a TPM chip, which not all systems have.
Alternatives to BitLocker
If BitLocker isn't the right fit for you, several alternatives exist that may have more features for you. VeraCrypt is a free, open-source encryption tool with advanced security features that allows you to encrypt hidden drives. AxCrypt offers simple file encryption for everyday users, allowing Explorer integration to encrypt on a file level and give you greater control. DiskCryptor provides another open-source solution for full-drive security. Mac users can rely on FileVault, while Linux users have LUKS as their go-to encryption method.
Geek Verdict
BitLocker is an excellent encryption solution for Windows users looking for strong, hardware-backed security. While it has some limitations, its seamless integration and robust encryption make it a reliable option for businesses, government agencies, and individuals alike. If you're using Windows Pro or Enterprise, BitLocker is an easy way to protect your data—just make sure you don't lose your recovery key!
Pro Tip: If you want security without most of the hassle of encrypting your entire drive, leave C: unencrypted for Windows and create a separate partition for sensitive files. Just encrypt the secondary partition with BitLocker, and whenever you need access, enter your password or use a recovery key. Open BitLocker in the Control Panel, find the partition you want to encrypt, and follow the prompts. It's the best of both worlds—fast boot times and strong encryption where it matters most. The bonus is that a separately encrypted partition is generally less likely to run into BitLocker password or recovery key issues due to updates and minor changes than encrypting the entire system drive (C
Got questions? Tips? Advice? Bitlocker horror stories? Drop them in the comments.
comments powered by Disqus






